Over the past decade, phishing simulations have become a mainstay in organisational cybersecurity aw...


Over the past decade, phishing simulations have become a mainstay in organisational cybersecurity aw...
Here are five reasons why secure coding and defence-in-depth are still necessary even if you have a ...

Over the years, I've witnessed a transformation in the way organisations approach information securi...

Amazon Cognito User Pools are capable of issuing identity tokens in the form of JSON Web Tokens (JWT...

In the world of web development, JSON Web Tokens (JWTs) have become a popular choice for securely tr...

Do you have redundant or unused services in your microservices architecture?

Performing a security audit of cloud infrastructure provides numerous benefits, ensuring the robustn...

👩💼 Senior manager: How long do you need to deliver Feature X? Software developer: That will take ...
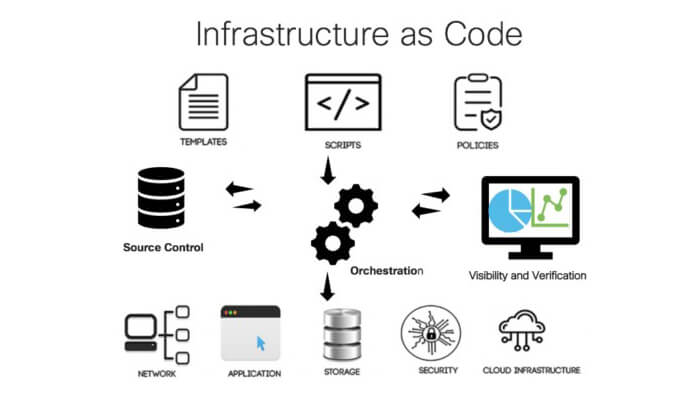
Discover the concept of infrastructure-as-code and its importance in modern IT operations.

Do you understand the emerging new standard in network security - Zero Trust Security Model? Learn h...